Getting Serious About Online Personal Security - Two-Factor Authentication
This is the second post in a series about personal online security. This post is about a security measure called two-factor authentication. Two-factor authentication is about adding a second layer of security to your online accounts and will be described in more detail below. You can find the other parts of the series listed below.
- Passwords
- Two-Factor Authentication (this post)
- Linked Accounts (coming soon)
- Trusted Devices (coming soon)
- Mobile Devices (coming soon)
- Backup (coming soon)
What is Two-Factor Authentication
Two-factor authentication describes a system that requires users to present two different methods of verification before gaining access to a secured resource. This is generally implemented via a knowledge factor and a possession factor. The knowledge factor is something you are already familiar with and use regularly This is your username and password. The second factor of authentication or possession factor, is generally implemented using your mobile phone either through an app that generates a time based pin code or via receiving a text message with a pin code.
By adding this second possession factor of authentication to your account you are making it extremely difficult for somebody to compromise your account even if they have your password. Gaining access to an account with two-factor authentication enabled requires that malicious user have both your password and access to your mobile device.
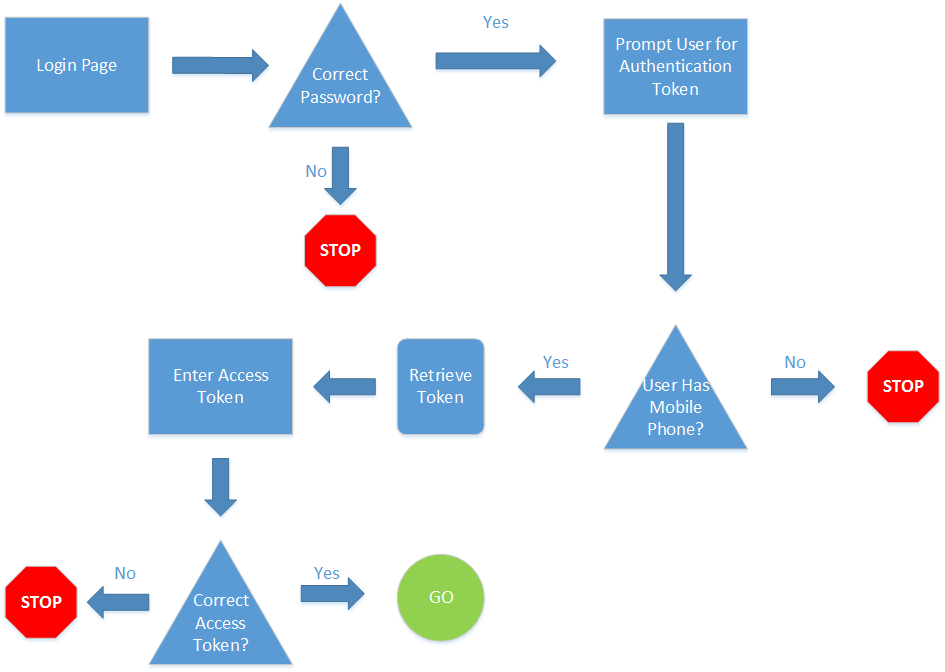
This may all sound complicated, but it is really quite simple. The authentication process for two-factor authentication can be seen in the diagram below.
The beauty of this process is that there are multiple points where a malicious user may be stopped. The bad thing is that it makes it more complicated for you to authenticate. However, most service who have implemented two factor authentication have also added steps to lessen the burden for legitimate users. For example, Google allow you to trust a computer for 30 days so you only have to use the two-factor authentication step once a month on a computer you use every day.
Real World Example
The diagram above shows how two-factor authentication works in theory. Below I will walk you through the steps for using two-factor authentication on a real account, in this case my Google Account.
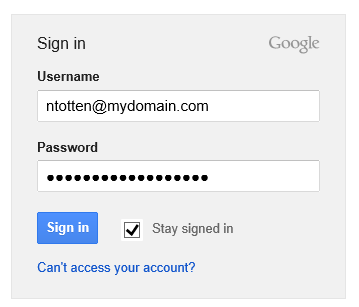
The first authentication step is the same for everyone regardless if you are using two-factor authentication or not. You must enter your Google Account username and password.
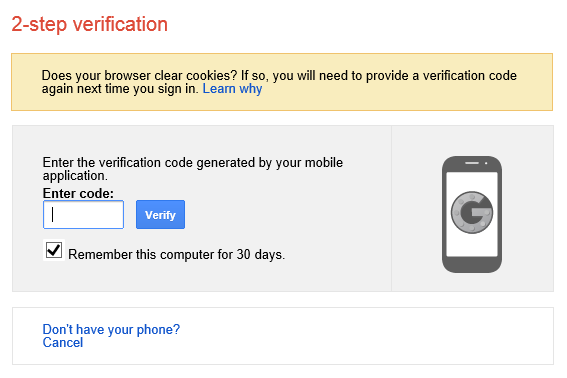
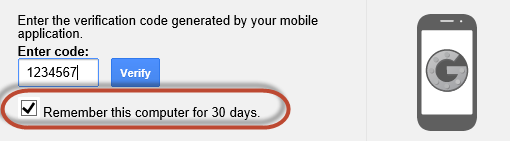
After you successfully authenticate with your Google username and password you will be prompted for a code.
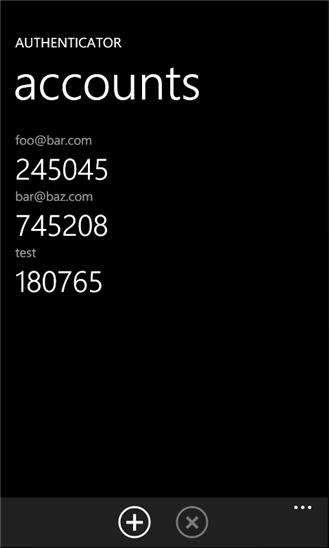
If you have your phone with you you will either use an app to generate a code or receive a text message. This depends on how you have setup Google two-factor authentication. I will go into more detail below. In my case, I use an app that generates a code. These codes are time-based and are only valid for about 30 seconds.
Next, simply enter the code and click verify. If you are the only user of the computer, you can check the box to remember the computer for 30 days. This way you won’t have to perform this verification every time you want to check your Gmail.
What if you don’t have your phone?
The one issue I get asked most about this process is what if you don’t have your phone. The short answer is that you won’t be able to access your account. As this is making your account secure, this is exactly what you want! However, there might be some emergency situation where you absolutely need to get into your account that is protected by two-factor authentication. Ultimately, each provider will have different options for gaining access to an account without the access code, but it will be possible. It is just usually fairly difficult. For example, Facebook requires you to email them a copy of you holding your drivers license so they can match your face with the information on your drivers license and Facebook account. Google makes it a bit easier by allowing you to specify a backup phone number to receive a SMS code. For example you could make your wife or parent’s phone a backup in case you don’t have your phone available.
Either way, it will be difficult to get into your account if you don’t have your phone, but you wont be locked out forever. Remember though, this is exactly the point. You want to make it more difficult for someone to gain access to your account.
Enabling Two-Factor Authentication
Each provide that supports two-factor authentication has different instructions for enabling it. Below you will find links to instructions for some of the most common services that support two-factor authentication or similar security measures.
- Dropbox
- Yahoo
- Microsoft (Hotmail, Outlook, Xbox, etc.)
- PayPal
- Amazon Web Services
- DNSimple
Next Steps
- Passwords
- Two-Factor Authentication (this post)
- Linked Accounts (coming soon)
- Trusted Devices (coming soon)
- Mobile Devices (coming soon)
- Backup (coming soon)